内网穿透
nps
项目:https://github.com/ehang-io/nps
文档:https://ehang-io.github.io/nps
1.启动服务器
服务器会占用80 443 8080(web) 8042(客户端连接)
启动服务器
创建一个客户端
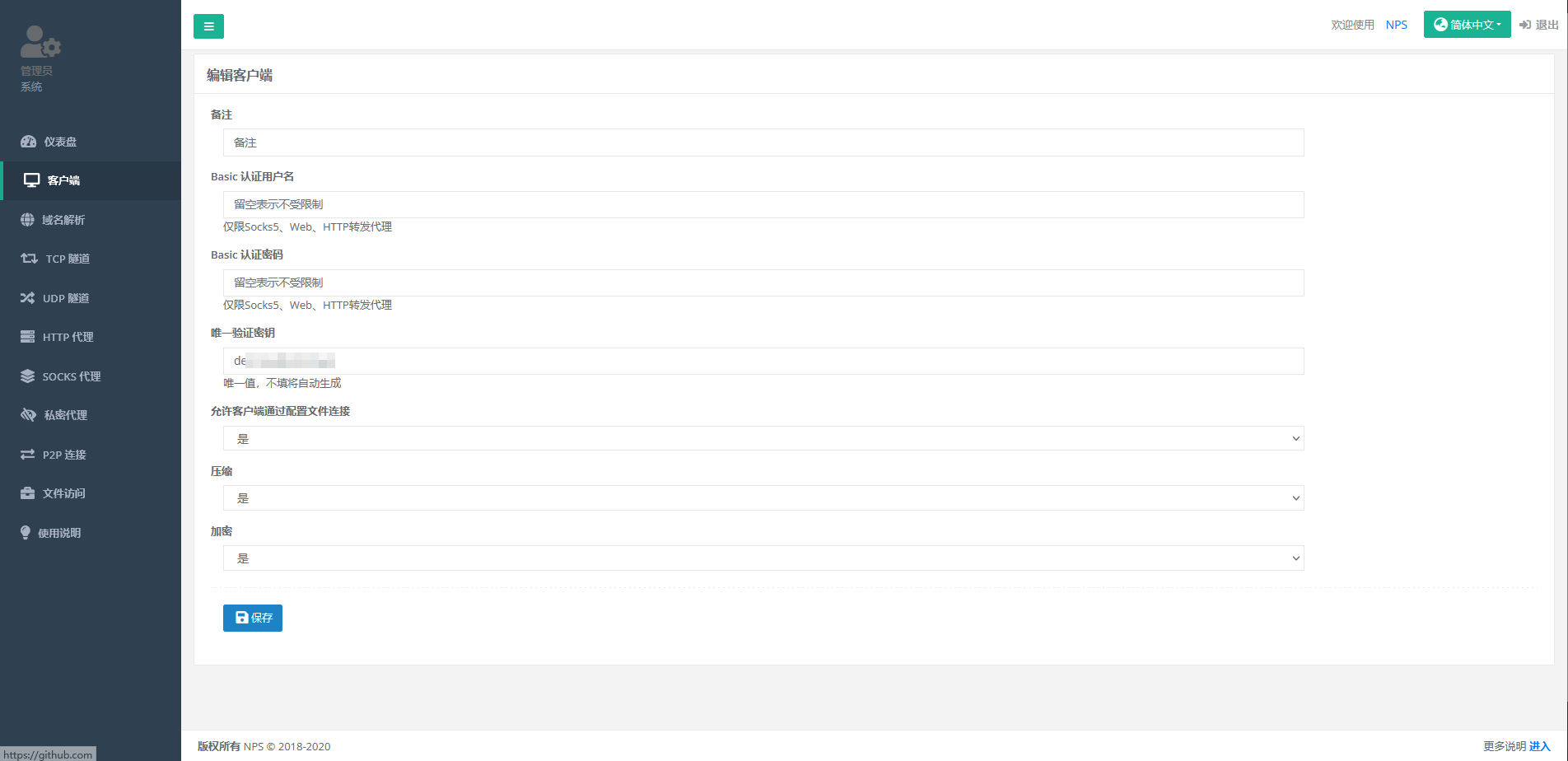
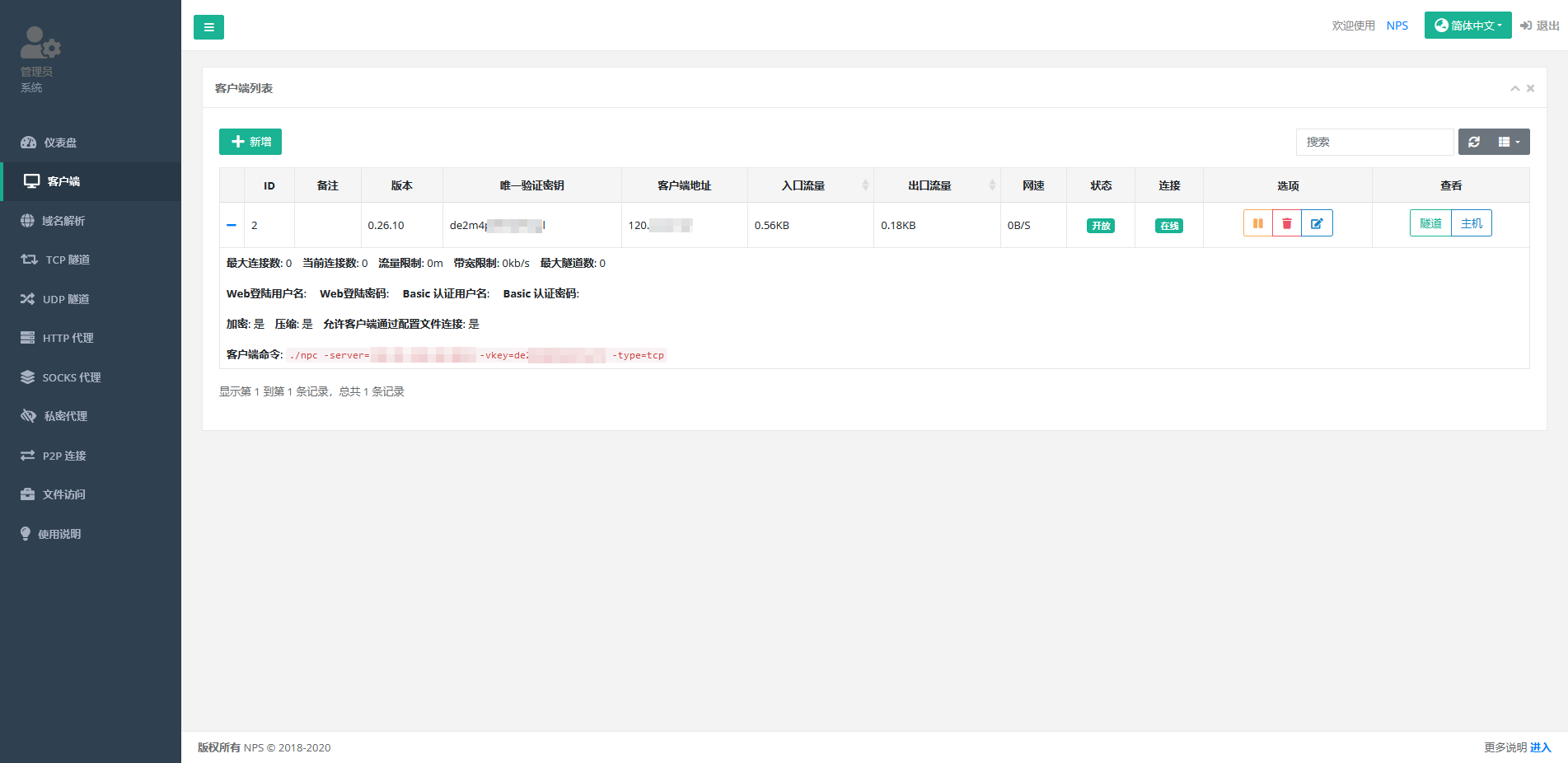
客户端命令:./npc -server=xxx.xxx.xxx.xxx:8024 -vkey=de2xxxxxxxx -type=tcp
2.TCP隧道

服务端端口:通过公网IP访问的端口
目标 (IP:端口):局域网内的IP和端口
服务端配置无需修改
启动客户端
1
| ./npc -server=xxx.xxx.xxx.xxx:8024 -vkey=de2mxxxxxxx -type=tcp
|
3.域名解析

域名申请和证书的制作参考acme使用ZeroSSL申请泛域名
主机:绑定主机IP的域名
模式:http(通过nginx代理转到http端口)
目标 (IP:端口):局域网内的IP和端口
修改nps配置
1
2
3
4
5
6
7
8
9
| appname = nps
#Boot mode(dev|pro)
runmode = dev
#HTTP(S) proxy port, no startup if empty
http_proxy_ip=0.0.0.0
http_proxy_port=8000 #需要改成非80端口,nginx转发到这个端口
https_proxy_port= # 设置为空来关闭https
https_just_proxy=true
|
安装nginx
1
2
| apt install socat
apt install nginx
|
nginx配置
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
|
upstream nps {
server 127.0.0.1:8000;
}
server {
listen 80;
server_name test.vper.ml;
rewrite ^(.*)$ https://$host$1 permanent;
}
server {
listen 443 ssl;
server_name test.vper.ml;
root /www/web/test.vper.ml;
index index.html index.htm;
ssl_certificate /root/cert/fullchain.cer;
ssl_certificate_key /root/cert/*.vper.ml.key;
ssl_session_timeout 5m;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA;
ssl_session_cache shared:SSL:50m;
ssl_prefer_server_ciphers on;
location / {
proxy_set_header Host $http_host;
proxy_pass http://nps;
}
}
|
重启nginx
启动服务器
启动客户端
1
| ./npc -server=xxx.xxx.xxx.xxx:8024 -vkey=de2xxxxxxxx -type=tcp
|
frp
https://github.com/fatedier/frp






